抓包分析中判断tcp连接开始和断开
发布日期:2021-06-30 22:18:00
浏览次数:2
分类:技术文章
本文共 30324 字,大约阅读时间需要 101 分钟。
前言
在cm中看到, 在判断是tcp结束包时,要做收尾的任务。
在实际运行中, 却发现经常不进行收尾工作,概率还挺高的。 那只能说明,没检测到tcp结束包。 抓了一个完整包,在wireshark中分析,学习下人家怎么玩的。 突然想到,去看下cm中怎么判断tcp结束包的?虽然那是个最基础的代码,还是去确认一下。 看了以后,在wireshark中找到tcp结束包,比对了一下,才明白,cm中判断tcp结束包,居然写错了… wireshark看tcp握手包和结束包,虽然是多个交互。但是可以根据一个包就能大致判断出是已经握手了,还是已经结束了。不用再去判断上下文。实验
握手包
握手包,只要tcp头标志出现SYN(同步) + ACK(确认),tcp连接就开始了。这个包是服务器回给客户端的.
Transmission Control Protocol, Src Port: 3306, Dst Port: 25304, Seq: 0, Ack: 1, Len: 0 Source Port: 3306 Destination Port: 25304 [Stream index: 0] [TCP Segment Len: 0] Sequence number: 0 (relative sequence number) [Next sequence number: 0 (relative sequence number)] Acknowledgment number: 1 (relative ack number) 1000 .... = Header Length: 32 bytes (8) Flags: 0x012 (SYN, ACK) 000. .... .... = Reserved: Not set ...0 .... .... = Nonce: Not set .... 0... .... = Congestion Window Reduced (CWR): Not set .... .0.. .... = ECN-Echo: Not set .... ..0. .... = Urgent: Not set .... ...1 .... = Acknowledgment: Set .... .... 0... = Push: Not set .... .... .0.. = Reset: Not set .... .... ..1. = Syn: Set .... .... ...0 = Fin: Not set [TCP Flags: ·······A··S·] Window size value: 14600 [Calculated window size: 14600] Checksum: 0x4341 [unverified] [Checksum Status: Unverified] Urgent pointer: 0 Options: (12 bytes), Maximum segment size, No-Operation (NOP), No-Operation (NOP), SACK permitted, No-Operation (NOP), Window scale [SEQ/ACK analysis] [Timestamps]
结束包
结束包,只要tcp头标志出现FIN(结束) + ACK(确认),tcp连接就结束了。这个包是服务器和客户端都要回给对方的。
只要有一家说要结束,就表明要结束了.Transmission Control Protocol, Src Port: 25304, Dst Port: 3306, Seq: 181, Ack: 731, Len: 0 Source Port: 25304 Destination Port: 3306 [Stream index: 0] [TCP Segment Len: 0] Sequence number: 181 (relative sequence number) [Next sequence number: 181 (relative sequence number)] Acknowledgment number: 731 (relative ack number) 0101 .... = Header Length: 20 bytes (5) Flags: 0x011 (FIN, ACK) 000. .... .... = Reserved: Not set ...0 .... .... = Nonce: Not set .... 0... .... = Congestion Window Reduced (CWR): Not set .... .0.. .... = ECN-Echo: Not set .... ..0. .... = Urgent: Not set .... ...1 .... = Acknowledgment: Set .... .... 0... = Push: Not set .... .... .0.. = Reset: Not set .... .... ..0. = Syn: Not set .... .... ...1 = Fin: Set [TCP Flags: ·······A···F] Window size value: 253 [Calculated window size: 64768] [Window size scaling factor: 256] Checksum: 0xb88d [unverified] [Checksum Status: Unverified] Urgent pointer: 0 [Timestamps]
工程下载点
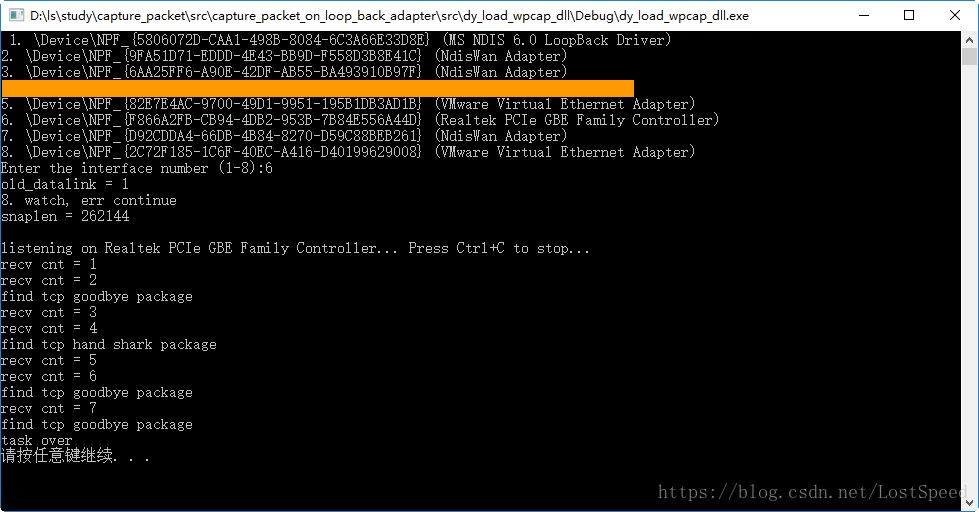
写了个demo来验证开始包和结束包数的对不对,用打出的信息和wireshark打开的捕获后的pcap文件对了一下,开始包和结束包这样判断是对的,完全对的上。
根据计算机的不同,开始包和结束包有重传的现象.运行效果
工程预览
// dy_load_wpcap_dll.cpp : Defines the entry point for the console application.//#include "stdafx.h"#include "wpcap_dll_ex.h"// please declare _CRT_SECURE_NO_WARNING on project#ifndef MYLOG_I#define MYLOG_I printf#endif#includetypedef uint32_t addr_t;typedef uint16_t port_t;// @ref https://stackoverflow.com/questions/16519846/parse-ip-and-tcp-header-especially-common-tcp-header-optionsof-packets-capture#pragma pack(push, 1)typedef struct { u_char dst_addr[6]; u_char src_addr[6]; u_short type;} TAG_ETHER_HEADER;typedef struct { uint8_t ver_ihl; // 4 bits version and 4 bits internet header length uint8_t tos; uint16_t total_length; uint16_t id; uint16_t flags_fo; // 3 bits flags and 13 bits fragment-offset uint8_t ttl; uint8_t protocol; uint16_t checksum; addr_t src_addr; addr_t dst_addr;} TAG_IP_HEADER;typedef struct { uint16_t src_port; uint16_t dst_port; uint32_t seq; uint32_t ack; uint8_t data_offset; // 4 bits uint8_t flags; uint16_t window_size; uint16_t checksum; uint16_t urgent_p;} TAG_TCP_HEADER;/*TAG_TCP_HEADER.flagsFlags: 0x011 (FIN, ACK)000. .... .... = Reserved: Not set...0 .... .... = Nonce: Not set.... 0... .... = Congestion Window Reduced (CWR): Not set.... .0.. .... = ECN-Echo: Not set.... ..0. .... = Urgent: Not set.... ...1 .... = Acknowledgment: Set.... .... 0... = Push: Not set.... .... .0.. = Reset: Not set.... .... ..0. = Syn: Not set.... .... ...1 = Fin: Set[TCP Flags: ·······A···F]*/#define FLAG_BIT_TCP_FIN 0x01#define FLAG_BIT_TCP_SYN 0x02#define FLAG_BIT_TCP_ACK 0x10typedef struct { uint8_t kind; uint8_t size;} TAG_TCP_OPTION;typedef struct { port_t src_port; port_t dst_port; uint16_t length; uint16_t checksum;} TAG_UDP_HEADER;#pragma pack(pop)#define PCAP_FILE_DUMP_TO "c:\\test\\abc.pcap"#define MY_CAPTRUE_FILTER "tcp"pcap_t* adhandle = NULL;pcap_dumper_t* dumpfile = NULL;struct bpf_program my_bpf_program;bool b_valid_bpf = false;void packet_handler(u_char *dumpfile, const struct pcap_pkthdr *header, const u_char *pkt_data);void print_packet(const char* psz_tip, const char* pdata, int iLen);char get_hex_char_to_disp(u_char c);bool is_char_can_print(char c);BOOL WINAPI phandler_routine(DWORD CtrlType){ BOOL rc = FALSE; switch (CtrlType) { case CTRL_C_EVENT: { if (NULL != adhandle) { pcap_breakloop(adhandle); } } rc = TRUE; break; default: break; } return rc;}int _tmain(int argc, _TCHAR* argv[]){ bool rc = false; pcap_if_t *alldevs = NULL; pcap_if_t *d = NULL; int inum = 0; int i = 0; char errbuf[PCAP_ERRBUF_SIZE] = { '\0'}; do { if (!fn_dy_load_wpcap()) { break; } if (!SetConsoleCtrlHandler(phandler_routine, TRUE)) { break; } /* Retrieve the device list on the local machine */ if (pcap_findalldevs(&alldevs, errbuf) == -1) { fprintf(stderr, "Error in pcap_findalldevs: %s\n", errbuf); exit(1); } /* Print the list */ for (d = alldevs; d; d = d->next) { printf("%d. %s", ++i, d->name); if (d->description) printf(" (%s)\n", d->description); else printf(" (No description available)\n"); } if (i == 0) { printf("\nNo interfaces found! Make sure WinPcap is installed.\n"); return -1; } printf("Enter the interface number (1-%d):", i); scanf_s("%d", &inum); if (inum < 1 || inum > i) { printf("\nInterface number out of range.\n"); /* Free the device list */ pcap_freealldevs(alldevs); return -1; } /* Jump to the selected adapter */ for (d = alldevs, i = 0; i< inum - 1; d = d->next, i++); // 走这里了 // argv[2] is netcard name adhandle = pcap_create(d->name, errbuf); if (NULL == adhandle) { printf("5. watch\n"); return -1; } pcap_set_promisc(adhandle, 1); // interface_opts->promisc_mode is 1 pcap_set_timeout(adhandle, -1); // timeout is 250 pcap_set_buffer_size(adhandle, 10 * 1024 * 1024); int err = 0; err = pcap_activate(adhandle); if (0 != err) { printf("7. watch\n"); return -1; } int old_datalink = pcap_datalink(adhandle); printf("old_datalink = %d\n", old_datalink); if (0 != old_datalink) { err = pcap_set_datalink(adhandle, 0); if (0 != err) { printf("8. watch, err continue\n"); // return -1; } } // capture_loop_init_filter int snaplen = pcap_snapshot(adhandle); printf("snaplen = %d\n", snaplen); /* Open the device */ //if ( (adhandle= pcap_open(d->name, // name of the device // 65536, // portion of the packet to capture // // 65536 guarantees that the whole packet will be captured on all the link layers // PCAP_OPENFLAG_PROMISCUOUS, // promiscuous mode // 1000, // read timeout // NULL, // authentication on the remote machine // errbuf // error buffer // ) ) == NULL) //{ // fprintf(stderr,"\nUnable to open the adapter. %s is not supported by WinPcap\n", d->name); // /* Free the device list */ // pcap_freealldevs(alldevs); // return -1; //} /* Open the dump file */ dumpfile = pcap_dump_open(adhandle, PCAP_FILE_DUMP_TO); if (dumpfile == NULL) { fprintf(stderr, "\nError opening output file\n"); return -1; } printf("\nlistening on %s... Press Ctrl+C to stop...\n", d->description); /* At this point, we no longer need the device list. Free it */ pcap_freealldevs(alldevs); // compile BPF if (pcap_compile(adhandle, &my_bpf_program, MY_CAPTRUE_FILTER, 1, 0) == -1) { fprintf(stderr, "error\n"); break; } b_valid_bpf = true; // set BPF filter if (pcap_setfilter(adhandle, &my_bpf_program) == -1) { fprintf(stderr, "error\n"); break; } /* start the capture */ pcap_loop(adhandle, 0, packet_handler, (unsigned char *)dumpfile); printf("task over\n"); rc = true; } while (0); if (!rc) { printf("error happen\n"); } if (NULL != dumpfile) { pcap_dump_close(dumpfile); dumpfile = NULL; } if (b_valid_bpf) { b_valid_bpf = false; pcap_freecode(&my_bpf_program); } if (NULL != adhandle) { pcap_close(adhandle); adhandle = NULL; } system("pause"); return 0;}/* Callback function invoked by libpcap for every incoming packet */void packet_handler(u_char *dumpfile, const struct pcap_pkthdr *header, const u_char *pkt_data){ /* save the packet on the dump file */ // 假设抓的都是tcp的包数据 static int cnt = 0; const u_char* pc_data_left = NULL; // 没处理的数据 int len_data_left = 0; // 没处理的数据长度 TAG_ETHER_HEADER* p_ether_hdr = NULL; TAG_IP_HEADER* p_ip_hdr = NULL; TAG_TCP_HEADER* p_tcp_hdr = NULL; int ip_header_size = 0; bool is_process_ok = false; do { cnt++; printf("recv cnt = %d\n", cnt); // print_packet("recv", (const char*)pkt_data, header->caplen); pcap_dump(dumpfile, header, pkt_data); // 要保存一份抓包文件,用于比对分析结果 if ((NULL == dumpfile) || (NULL == header) || (NULL == pkt_data)) { printf("error\n"); break; } len_data_left = header->caplen; pc_data_left = pkt_data; // remove ether header from data in if (len_data_left < (int)sizeof(TAG_ETHER_HEADER)) { printf("error\n"); break; } p_ether_hdr = (TAG_ETHER_HEADER*)pc_data_left; pc_data_left += sizeof(TAG_ETHER_HEADER); len_data_left -= sizeof(TAG_ETHER_HEADER); // remove ip header from data in if (len_data_left < (int)sizeof(TAG_IP_HEADER)) { printf("error\n"); break; } p_ip_hdr = (TAG_IP_HEADER*)pc_data_left; ip_header_size = 4 * (p_ip_hdr->ver_ihl & 0x0F); pc_data_left += ip_header_size; len_data_left -= ip_header_size; // remove tcp header from data in if (len_data_left < (int)sizeof(TAG_TCP_HEADER)) { printf("error\n"); break; } p_tcp_hdr = (TAG_TCP_HEADER*)pc_data_left; pc_data_left += sizeof(TAG_TCP_HEADER); len_data_left -= sizeof(TAG_TCP_HEADER); // print_packet("tcp payload", (const char*)pc_data_left, len_data_left); if ( ((p_tcp_hdr->flags & FLAG_BIT_TCP_SYN) > 0) && ((p_tcp_hdr->flags & FLAG_BIT_TCP_ACK) > 0)) { printf("find tcp hand shark package\n"); } else if (((p_tcp_hdr->flags & FLAG_BIT_TCP_FIN) > 0) && ((p_tcp_hdr->flags & FLAG_BIT_TCP_ACK) > 0)) { printf("find tcp goodbye package\n"); } is_process_ok = true; } while (0); if (!is_process_ok) { if (NULL != adhandle) { pcap_breakloop(adhandle); } }}void print_packet(const char* psz_tip, const char* pdata, int iLen){ char szBuf[260] = { '\0' }; const int iOneRowChars = 16; const unsigned char* pCur = NULL; int iPos = 0; do { if (NULL == pdata) { break; } MYLOG_I("%s : %d(bytes)\n", ((NULL != psz_tip) && ((int)strlen(psz_tip) > 0)) ? psz_tip : "print_packet", iLen); do { pCur = (unsigned char*)(pdata + iPos); if (iLen >= iOneRowChars) { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X | %c%c%c%c%c%c%c%c%c%c%c%c%c%c%c%c", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), *(pCur + 4), *(pCur + 5), *(pCur + 6), *(pCur + 7), *(pCur + 8), *(pCur + 9), *(pCur + 10), *(pCur + 11), *(pCur + 12), *(pCur + 13), *(pCur + 14), *(pCur + 15), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3)), get_hex_char_to_disp(*(pCur + 4)), get_hex_char_to_disp(*(pCur + 5)), get_hex_char_to_disp(*(pCur + 6)), get_hex_char_to_disp(*(pCur + 7)), get_hex_char_to_disp(*(pCur + 8)), get_hex_char_to_disp(*(pCur + 9)), get_hex_char_to_disp(*(pCur + 10)), get_hex_char_to_disp(*(pCur + 11)), get_hex_char_to_disp(*(pCur + 12)), get_hex_char_to_disp(*(pCur + 13)), get_hex_char_to_disp(*(pCur + 14)), get_hex_char_to_disp(*(pCur + 15))); MYLOG_I("%s\n", szBuf); iPos += iOneRowChars; iLen -= iOneRowChars; } else { switch (iLen) { case 15: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X | %c%c%c%c%c%c%c%c%c%c%c%c%c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), *(pCur + 4), *(pCur + 5), *(pCur + 6), *(pCur + 7), *(pCur + 8), *(pCur + 9), *(pCur + 10), *(pCur + 11), *(pCur + 12), *(pCur + 13), *(pCur + 14), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3)), get_hex_char_to_disp(*(pCur + 4)), get_hex_char_to_disp(*(pCur + 5)), get_hex_char_to_disp(*(pCur + 6)), get_hex_char_to_disp(*(pCur + 7)), get_hex_char_to_disp(*(pCur + 8)), get_hex_char_to_disp(*(pCur + 9)), get_hex_char_to_disp(*(pCur + 10)), get_hex_char_to_disp(*(pCur + 11)), get_hex_char_to_disp(*(pCur + 12)), get_hex_char_to_disp(*(pCur + 13)), get_hex_char_to_disp(*(pCur + 14))); MYLOG_I("%s\n", szBuf); } break; case 14: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X | %c%c%c%c%c%c%c%c%c%c%c%c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), *(pCur + 4), *(pCur + 5), *(pCur + 6), *(pCur + 7), *(pCur + 8), *(pCur + 9), *(pCur + 10), *(pCur + 11), *(pCur + 12), *(pCur + 13), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3)), get_hex_char_to_disp(*(pCur + 4)), get_hex_char_to_disp(*(pCur + 5)), get_hex_char_to_disp(*(pCur + 6)), get_hex_char_to_disp(*(pCur + 7)), get_hex_char_to_disp(*(pCur + 8)), get_hex_char_to_disp(*(pCur + 9)), get_hex_char_to_disp(*(pCur + 10)), get_hex_char_to_disp(*(pCur + 11)), get_hex_char_to_disp(*(pCur + 12)), get_hex_char_to_disp(*(pCur + 13))); MYLOG_I("%s\n", szBuf); } break; case 13: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X | %c%c%c%c%c%c%c%c%c%c%c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), *(pCur + 4), *(pCur + 5), *(pCur + 6), *(pCur + 7), *(pCur + 8), *(pCur + 9), *(pCur + 10), *(pCur + 11), *(pCur + 12), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3)), get_hex_char_to_disp(*(pCur + 4)), get_hex_char_to_disp(*(pCur + 5)), get_hex_char_to_disp(*(pCur + 6)), get_hex_char_to_disp(*(pCur + 7)), get_hex_char_to_disp(*(pCur + 8)), get_hex_char_to_disp(*(pCur + 9)), get_hex_char_to_disp(*(pCur + 10)), get_hex_char_to_disp(*(pCur + 11)), get_hex_char_to_disp(*(pCur + 12))); MYLOG_I("%s\n", szBuf); } break; case 12: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X | %c%c%c%c%c%c%c%c%c%c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), *(pCur + 4), *(pCur + 5), *(pCur + 6), *(pCur + 7), *(pCur + 8), *(pCur + 9), *(pCur + 10), *(pCur + 11), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3)), get_hex_char_to_disp(*(pCur + 4)), get_hex_char_to_disp(*(pCur + 5)), get_hex_char_to_disp(*(pCur + 6)), get_hex_char_to_disp(*(pCur + 7)), get_hex_char_to_disp(*(pCur + 8)), get_hex_char_to_disp(*(pCur + 9)), get_hex_char_to_disp(*(pCur + 10)), get_hex_char_to_disp(*(pCur + 11))); MYLOG_I("%s\n", szBuf); } break; case 11: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X | %c%c%c%c%c%c%c%c%c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), *(pCur + 4), *(pCur + 5), *(pCur + 6), *(pCur + 7), *(pCur + 8), *(pCur + 9), *(pCur + 10), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3)), get_hex_char_to_disp(*(pCur + 4)), get_hex_char_to_disp(*(pCur + 5)), get_hex_char_to_disp(*(pCur + 6)), get_hex_char_to_disp(*(pCur + 7)), get_hex_char_to_disp(*(pCur + 8)), get_hex_char_to_disp(*(pCur + 9)), get_hex_char_to_disp(*(pCur + 10))); MYLOG_I("%s\n", szBuf); } break; case 10: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X | %c%c%c%c%c%c%c%c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), *(pCur + 4), *(pCur + 5), *(pCur + 6), *(pCur + 7), *(pCur + 8), *(pCur + 9), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3)), get_hex_char_to_disp(*(pCur + 4)), get_hex_char_to_disp(*(pCur + 5)), get_hex_char_to_disp(*(pCur + 6)), get_hex_char_to_disp(*(pCur + 7)), get_hex_char_to_disp(*(pCur + 8)), get_hex_char_to_disp(*(pCur + 9))); MYLOG_I("%s\n", szBuf); } break; case 9: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X | %c%c%c%c%c%c%c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), *(pCur + 4), *(pCur + 5), *(pCur + 6), *(pCur + 7), *(pCur + 8), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3)), get_hex_char_to_disp(*(pCur + 4)), get_hex_char_to_disp(*(pCur + 5)), get_hex_char_to_disp(*(pCur + 6)), get_hex_char_to_disp(*(pCur + 7)), get_hex_char_to_disp(*(pCur + 8))); MYLOG_I("%s\n", szBuf); } break; case 8: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X | %c%c%c%c%c%c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), *(pCur + 4), *(pCur + 5), *(pCur + 6), *(pCur + 7), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3)), get_hex_char_to_disp(*(pCur + 4)), get_hex_char_to_disp(*(pCur + 5)), get_hex_char_to_disp(*(pCur + 6)), get_hex_char_to_disp(*(pCur + 7))); MYLOG_I("%s\n", szBuf); } break; case 7: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X %2.2X %2.2X %2.2X | %c%c%c%c%c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), *(pCur + 4), *(pCur + 5), *(pCur + 6), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3)), get_hex_char_to_disp(*(pCur + 4)), get_hex_char_to_disp(*(pCur + 5)), get_hex_char_to_disp(*(pCur + 6))); MYLOG_I("%s\n", szBuf); } break; case 6: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X %2.2X %2.2X | %c%c%c%c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), *(pCur + 4), *(pCur + 5), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3)), get_hex_char_to_disp(*(pCur + 4)), get_hex_char_to_disp(*(pCur + 5))); MYLOG_I("%s\n", szBuf); } break; case 5: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X %2.2X | %c%c%c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), *(pCur + 4), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3)), get_hex_char_to_disp(*(pCur + 4))); MYLOG_I("%s\n", szBuf); } break; case 4: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X %2.2X | %c%c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), *(pCur + 3), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2)), get_hex_char_to_disp(*(pCur + 3))); MYLOG_I("%s\n", szBuf); } break; case 3: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X %2.2X | %c%c%c ", *(pCur + 0), *(pCur + 1), *(pCur + 2), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1)), get_hex_char_to_disp(*(pCur + 2))); MYLOG_I("%s\n", szBuf); } break; case 2: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X %2.2X | %c%c ", *(pCur + 0), *(pCur + 1), get_hex_char_to_disp(*(pCur + 0)), get_hex_char_to_disp(*(pCur + 1))); MYLOG_I("%s\n", szBuf); } break; case 1: { sprintf_s(szBuf, sizeof(szBuf), "%2.2X | %c ", *(pCur + 0), get_hex_char_to_disp(*(pCur + 0))); MYLOG_I("%s\n", szBuf); } break; default: break; } iPos += iLen; iLen -= iLen; } } while (iLen > 0); } while (0);}bool is_char_can_print(char c){ return ((c >= 32) && (c < 127));}char get_hex_char_to_disp(u_char c){ char c_rc = '.'; if (is_char_can_print((char)c)) { c_rc = (char)c; } return c_rc;}
转载地址:https://lostspeed.blog.csdn.net/article/details/80843843 如侵犯您的版权,请留言回复原文章的地址,我们会给您删除此文章,给您带来不便请您谅解!
发表评论
最新留言
关注你微信了!
[***.104.42.241]2024年04月07日 15时44分02秒
关于作者

喝酒易醉,品茶养心,人生如梦,品茶悟道,何以解忧?唯有杜康!
-- 愿君每日到此一游!
推荐文章
关于java的枚举
2019-04-30
一个简单的layui登陆界面
2019-04-30
SQL考试常见题目
2019-04-30
使用Spring Boot写一个简单的Hello World
2019-04-30
Spring Boot整合Servlet使用
2019-04-30
SpringBoot 文件上传
2019-04-30
我居然在Github上找到了一个完整的停车系统(附源码地址)
2019-04-30
大厂经典面试题:Redis为什么这么快?
2019-04-30
培训班老师说可以用这个干掉一大批面试者
2019-04-30
阿里四面,居然栽在一道排序算法上
2019-04-30
【Java编码规范】《阿里巴巴Java开发手册(正式版)》发布!
2019-04-30
如何在二三线城市月薪过万(一)看完这篇后端简历优化,包你面试不断
2019-04-30
阿里P8大神教你十分钟构建好SpringBoot + SSM框架 成功晋升
2019-04-30
Linux运维-搭建高可用Redis缓存
2019-04-30
膜拜!阿里内部都在强推的K8S(kubernetes)学习指南,不能再详细了
2019-04-30
Linux 常用命令
2019-04-30
Android之Handler机制篇
2019-04-30
Android之RecyclerView篇
2019-04-30